AddThis Now Supports Sharing to Pinterest
November 22nd, 2011 by Kori Hill in Updates, Using AddThis, What's NewThis morning we are very excited to announce that AddThis now supports sharing to Pinterest! You can now start pinning interesting and fun images to your board.

Pinterest is a rapidly-growing image sharing social network which according to Businessweek has seen traffic grow 7x in the past 5 months. The site allows users to create “boards” for inspiration and has been furiously adopted by DIY crafters and bloggers.
![]()
To get your site set up with a Pinterest button follow the steps here. Please let us know if you have any questions!
Shirts Worth Sharing
November 18th, 2011 by jeffwongdesign in UncategorizedOur team wanted to take a moment to thank CustomInk for taking us on a tour of their office. They have one of the coolest spaces in Tysons Corner. They make great shirts and their team has a penchant for customer service. If you’re looking for inspiration or need to order some gear, check ‘em out.
AlwaysOn Venture Summit Top 100
November 17th, 2011 by Kori Hill in Milestones, Promotional(Originally posted on the Clearspring blog.)
Just a week away from Thanksgiving, we are counting our many blessings here at Clearspring. We’ve just been named among the AlwaysOn 2011 Venture Summit Mid-Atlantic Top 100 for being among the most promising private companies “creating new, vital solutions that will lead to industry disruption and huge value creation.” The honor stems from nominations by several top firms including Morgan Stanley, Technology Partners, DFJ, SAP and KPMG.
It’s great to be recognized, especially on the heels of a very busy past couple of months. In late September, we welcomed Ramsey McGrory, formerly of Yahoo! and RMX as our new CEO. In October, we took a look back at five years of sharing and analytics as we celebrated the fifth anniversary of our social sharing platform, AddThis (check us out in Adweek). Last week, AddThis hit another milestone as the largest social sharing platform – in a 24 hour period, we saw 3,000,000,000 (that’s 3 billion!) views. And, we recently announced our acquisition of data science company, XGraph. Together, we’ve created the largest multi-graph platform on the open web. By multi-graph, we mean that our understanding of an audience is multi-dimensional where a single-graph would only represent one dimension of how people are connected (like social ties, for instance). Based on 1.2 billion users, the extensive multi-graph capability has incredible implications for all of our partners across the board.
Whew! It’s been busy and we wouldn’t have it any other way. It couldn’t be more appropriate that all of this comes right before we each take a moment to give thanks. We are incredibly grateful to all of our clients, partners, investors and supporters. Thank you AlwaysOn, those that nominated and voted for us for this honor, and all of you for continuing to keep us motivated and inspired. As always, please reach out and let us know how we can better serve you.
It’s the Great Pumpkin, Clearspring!
November 4th, 2011 by Kori Hill in Fun(Originally posted on the Clearspring blog.)
It’s been a very busy week here at Clearspring with the announcement of XGraph joining the family. So busy, we didn’t get a chance to blog about our very first Halloween Costume Contest!
To give a quick rundown from some of our offices — Winnie the Pooh was spotted writing code and the iCloud was shedding “water droplets” all over the floors at HQ in McLean, VA. NYC was was raided by a zombie and a Richard Simmons exercise video extra showed up. LA even saw dead people.
Here are some pictures, including the winners of the three categories – Funniest, Scariest and Most Creative.
HQ’s Elizabeth Leiser won Most Creative with her rendition of the iCloud.
HQ’s Collin Hughes won Funniest for dressing up as fellow Clearspringer Ted Pearson. Here’s a reference:
LA’s Will Watson won Scariest for his interpretation of Dia de Los Muertos.
Some honorable mentions:
Rebecca Salerno of our NYC office dressed as a hostess turned zombie. She has rats in her hair!
NYC’s David S. just got back from filming his latest exercise video with Richard Simmons.
Charlie the Pooh.
Track Your StumbleUpon Clicks with AddThis Analytics
November 3rd, 2011 by Kori Hill in Using AddThis, What's NewStumbleUpon is one of the most popular sharing services on AddThis and can be an important driver of new traffic to your site. Now you can use AddThis analytics to track the number of clicks to your content from StumbleUpon, also known as “Stumbles”.
Just like our Facebook, bit.ly and Twitter integrations, you do not need to make any changes to start receiving StumbleUpon data. StumbleUpon stats are shown on the Content Detail page of the associated story, which you can find by clicking on any piece on content in your Analytics dashboard or from the Content tab.
If you have any feedback or requests for other 3rd party tracking services you would like to see in the AddThis Analytics, please post in the comments below or email us.
Welcome Aboard, XGraph!
November 1st, 2011 by susan in Milestones, PromotionalWe’re excited to announce that Clearspring has acquired XGraph!

XGraph is the leading data science company focused on modeling web-wide connections between people. Clearspring’s scalable data processing and massive reach via AddThis coupled with XGraph’s technology create the largest multi-graph platform on the open web—mapping 1.2 billion user’s connections by brand affiliation, intent and social behavior.
The social graph, the data structure that maps the connections we have with our friends, has taken the web by storm. This has proven to be a powerful platform, but this single graph only represents one dimension of how we are connected to one another. XGraph not only models these social connections, but also multiple other types of connections such as how we are related by brand affiliations, intent and more. This is the multi-graph.
With our new multi-graph platform, Clearspring has a truly differentiated capability to deliver powerful results to our publishers and advertisers. For publishers, we will use this graph platform to enable deeper audience insight, monetization and actionable data products in the near future. And, that’s just the beginning.
Thank you, as always, to our customers, partners and investors for making this possible. Welcome XGraph into the Clearspring family!
AddThis Integrates with Google Social Plugin Analytics
October 28th, 2011 by Greg Cypes in Tips, Using AddThis, What's NewWe know many of you out there use Google Analytics to help measure your site traffic and how users explore and engage with your content. We also know how you rely on AddThis to enable sharing and to provide social analytics for your website.
For publishers who use Google as their primary source for site analytics, injecting AddThis social insight data into Google Analytics enables you to analyze user interactions from our sharing tools as well as Facebook Like and Twitter Tweet right inside Google’s dashboard. Of course all of your real-time and rich audience data will still be available in your AddThis dashboard, too.
It is very easy to get AddThis for your site, and even easier to integrate Google Analytics. Get started today.
Twitter Mentions in AddThis Analytics Now in Real-Time
October 19th, 2011 by Kori Hill in Milestones, Using AddThis, What's NewAlong with our 5th birthday, AddThis is closing in on another fun milestone: 2 million Twitter followers! We wanted to say thanks to all our supporters today, particularly our Tweeps. We have loved connecting with you in 140 characters or less!
To celebrate, AddThis Analytics’ Twitter Mentions feature is now in real-time! This means anytime a URL from your domain is publicly tweeted, you will be able to see it – RIGHT when it’s been sent. You can find the Twitter Mentions on the Summary tab of your analytics as well as on each content detail page. See what people are saying on Twitter about your brand or specific content in real-time.
As always, we love hearing your feedback. What is your favorite part of the AddThis Analytics? What other pieces of data would you like to see that will help you understand the social interactions taking place on your site? We’re all ears!
25 Hours of Racing
October 12th, 2011 by Drew Stephens in Engineering, FunLast weekend the Clearspring Motor Club racing team, Cobra Kai, raced their Swedish Race Truck at Nelson Ledges Road Course in Ohio as part of the ChumpCar Longer Longest Day. After 25 hours, 25 minutes, and 25 seconds of racing—stopping only to change drivers and refuel the car every 2 hours—the checker flag dropped with our car in 13th place overall, a great result from a field of 74 cars that started the race.
ChumpCar is a racing series similar to the 24 Hours of LeMons. The premise is simple: buy a car for less than $500 and run it on a racetrack for hours on end. The car that accumulates the most laps over the race is declared the winner. This sort of “crap can” racing isn’t just orbiting a circle track, nor is it a demolition derby. The tracks are complex and difficult to master. The danger is real, too—we wear helmets, head-to-toe fire gear, all of the cars have full roll cages, and the safety rules are extensive.
In endurance racing the biggest factor is reliability. As long as you can keep out on the track without problems you have the basis for a good race. Performance can only take you so far and since the $500 price of the car includes any performance modifications, options there are limited. Our team has made great use of cutting things off of the car to improve performance. Before our first race we cut the springs and filled them with tennis balls to make the suspension stiffer. At our second race, the ChumpCar 24 Hours at VIR, we turned the race wagon into a truck by chopping the roof off while waiting in line to get into the racetrack. Our car’s performance from this weight-saving modification were enough to encourage another team at our most recent race to do the same with their Volvo.
Overall we had a great race without any problems that kept us off the track. Ending up in 13th place—ahead of dozens of cars that were turning faster laps when they were on track—is an wonderful achievement. For complete details on our race, check out this post on the CS Motor Club blog. Next time, we’re shooting for the top ten!
Think this is awesome? Check out the jobs page, we’re always looking for new drivers folks at Clearspring.
Happy Birthday AddThis!
October 11th, 2011 by Dominique Vonarburg in MilestonesThis month, we celebrate five years of sharing with AddThis. It began with a simple idea – make bookmarking and sharing easier. After a few months of coding, AddThis was born. At first, it was a single button with a few bookmarking services used by a few small publishers. But it quickly spread across the web and we started to see some interesting trends in how and what people share. With that information in hand, we introduced sharing analytics to offer this same insight to publishers.
In 2008, AddThis became part of Clearspring. Our vision was simple – create the web’s sharing platform. It took a lot of work, but together with you guys, we really made a dent in this goal. AddThis is now the largest content sharing platform on the web. Used by 10 million websites reaching over 1.2 billion people each month, the platform enables users to easily share to over 300 sharing destinations in over 70 languages. We are truly a global platform. Our in-house data processing capabilities, coupled with this huge reach, has put us in a great position to serve publishers in new and unique ways. This year, we introduced real-time analytics and the ability to track sharing that occurs via copy/paste actions on the address bar. The new suite of analytics helps publishers understand how people interact with their content right now, what their interests and influences are, and how they can increase engagement and social reach. With this same technology, we can derive insight into consumer interests and deliver more relevant advertising to users across the web. And that’s just the beginning.
Thank you so much for your loyalty and support over these last five years. It’s been an amazing ride and we are excited to work with you to have an even better next five years. In honor of our birthday, please enjoy this tasty infographic that captures some of what we’ve learned about sharing over the last half decade. Enjoy!
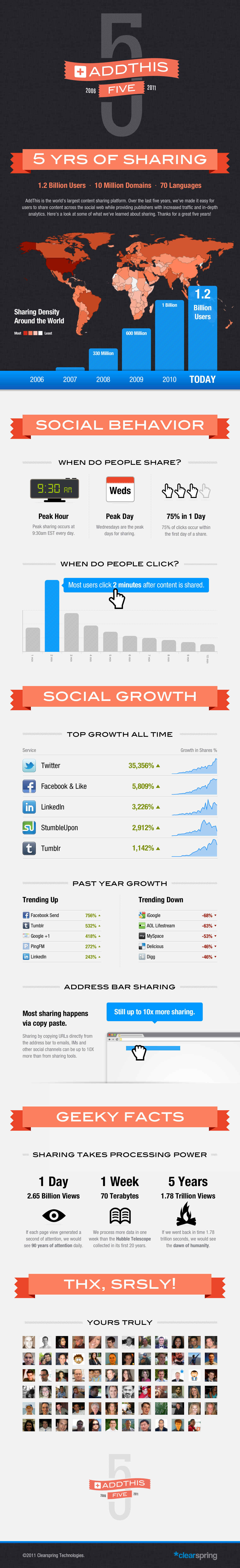
Note: We have replaced the originally posted infographic to reflect the correct number of unqiue users in 2008 to 330M.




















21 Comments